Monitoring, Logging And Runtime Security For Cks
Released 8/2025
By David Clinton
MP4 | Video: h264, 1280x720 | Audio: AAC, 44.1 KHz, 2 Ch
Level: Intermediate | Genre: eLearning | Language: English + subtitle | Duration: 1h 19m | Size: 157 MB
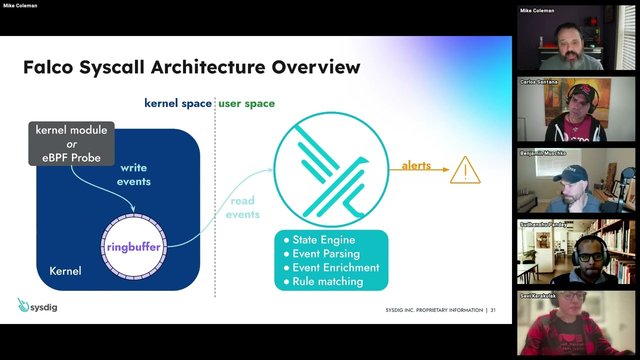
Up your Kubernetes security game with monitoring, logging, and runtime security skills tailored to the Certified Kubernetes Security Specialist (CKS) certification objectives. You'll learn how to perform behavioral analytics to identify malicious activities and detect threats across physical infrastructure, applications, networks, data, users, and workloads; investigate attack phases, identify bad actors, and implement measures to ensure container immutability at runtime, preventing unauthorized changes; and track activities, and enhance cluster security through proactive monitoring and analysis. By the end of this course, you'll be equipped to secure Kubernetes clusters by detecting and responding to threats, ensuring container immutability, and effectively using audit logs to monitor and protect your environment, preparing you for the CKS certification.